Discover Cutting-edge Protection with BQT Solutions for All Your Needs
Maximizing Business Defense: The Ultimate Overview to Electronic Protection Solutions
In the busy and ever-evolving landscape of organization safety and security, the dependence on electronic protection services has actually become vital for guarding valuable properties, private details, and maintaining operational connection. In this guide to electronic safety and security remedies, we will discover the newest trends, innovative modern technologies, and best practices to strengthen your service against prospective threats and vulnerabilities.
Importance of Electronic Protection Solutions
When considering the security of properties and delicate information, the importance of electronic security remedies can not be overemphasized. In today's interconnected globe, where cyber hazards are regularly progressing and coming to be more sophisticated, businesses must prioritize carrying out robust electronic safety and security steps to protect their data and procedures. Electronic security solutions incorporate a broad array of technologies and practices developed to safeguard versus unapproved access, information violations, malware, and various other cyber hazards.
One of the essential advantages of digital security solutions is their ability to offer real-time monitoring and hazard discovery. BQT Biometrics Australia. Through tools like breach detection systems, firewall programs, and protection information and occasion monitoring (SIEM) systems, companies can proactively determine and respond to security occurrences prior to they escalate into significant violations. In addition, electronic protection remedies help guarantee conformity with sector guidelines and standards, safeguarding companies from potential legal and monetary repercussions
Kinds Of Electronic Security Systems
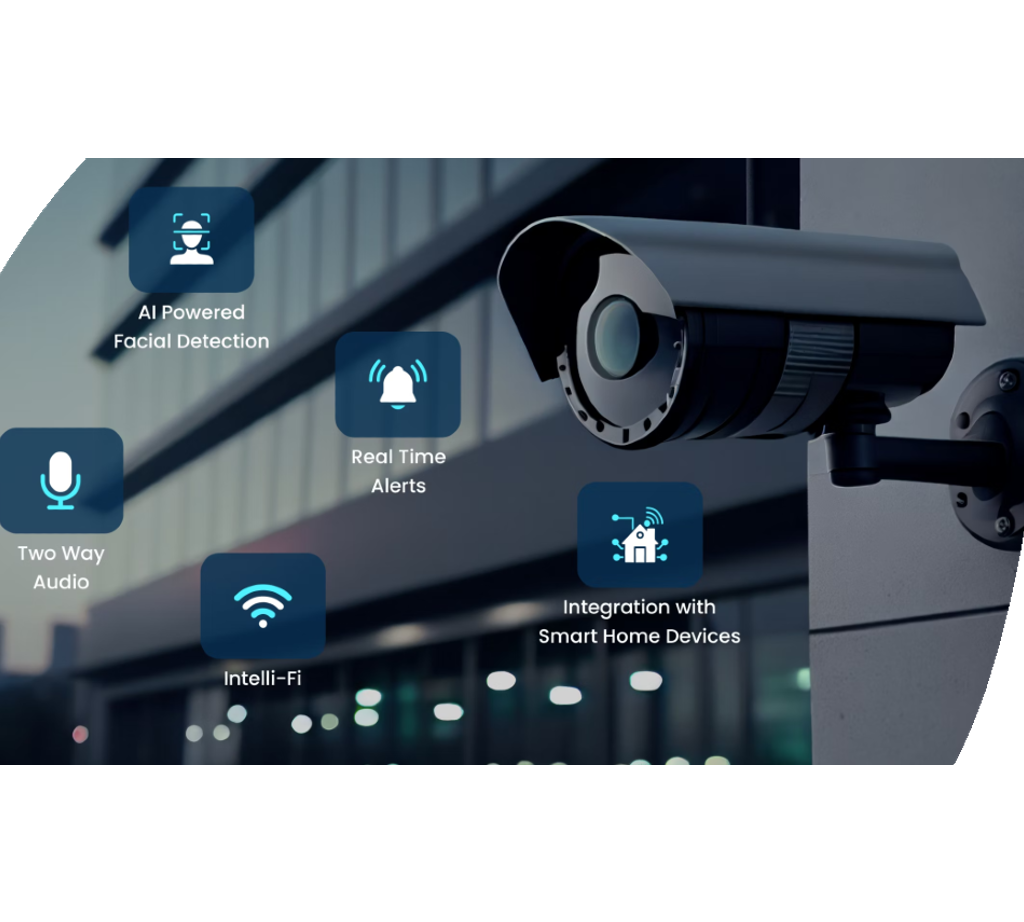
Offered the crucial importance of electronic security remedies in safeguarding businesses against cyber risks, it is important to check out the various kinds of digital safety systems offered to enhance security and strength. Among one of the most common sorts of digital protection systems is the firewall, which acts as a barrier between a company's inner network and outside networks, removing possibly harmful data. Breach Detection Solution (IDS) are likewise critical, as they monitor network traffic for suspicious task and sharp administrators to potential threats. In addition, businesses frequently count on security modern technologies to safeguard delicate information both at remainder and en route. Gain access to control systems, including biometric visitors and keycard access, aid manage entrance to physical areas and secure assets. Video monitoring systems play a role in surveillance and recording tasks within and around the properties. By utilizing a mix of these digital protection systems, organizations can develop a robust protection against different protection risks.
Implementing Accessibility Control Measures
Furthermore, access control actions can be integrated with monitoring systems to monitor and videotape people' movements within safeguarded areas. This integration enhances safety and security by offering an extensive review of who is accessing specific places at any kind of given time. In addition, access control systems can be configured to limit gain access to based on time, place, or specific credentials, enabling services to personalize safety procedures according to their specific demands.
Cybersecurity Best Practices
To enhance overall protection posture, carrying out durable cybersecurity ideal methods is imperative in guarding digital possessions and data integrity. One essential technique is making sure regular software program updates throughout all devices and systems to patch susceptabilities quickly. Using solid, web link distinct passwords and carrying out multi-factor verification adds layers of protection against unauthorized gain access to. Performing regular security audits and evaluations aids identify weaknesses and locations for enhancement. Worker training on cybersecurity recognition is crucial in avoiding social engineering strikes and guaranteeing a security-conscious labor force.
Establishing a thorough occurrence feedback plan makes it possible for swift and efficient actions to safety violations, reducing potential damage. Applying accessibility controls based on find more the concept of the very least privilege limits the exposure of critical systems and information to only those who need it for their roles. By including these ideal methods into cybersecurity strategies, businesses can strengthen their defenses against evolving cyber threats.
Security and Tracking Solutions

Video clip surveillance options supply remote tracking capacities, permitting authorized workers to watch on the premises even when off-site. Furthermore, progressed attributes like motion discovery, face recognition, and permit plate acknowledgment boost the overall safety and security pose of the organization. Integrating monitoring systems with alarm and access control even more enhances the safety framework, allowing an aggressive feedback to possible security breaches.
Conclusion
In conclusion, digital protection services find more info are crucial for making the most of business defense. It is crucial to invest in the appropriate electronic security systems to make sure the security and security of the company.